| Issue |
BIO Web Conf.
Volume 17, 2020
International Scientific-Practical Conference “Agriculture and Food Security: Technology, Innovation, Markets, Human Resources” (FIES 2019)
|
|
|---|---|---|
| Article Number | 00201 | |
| Number of page(s) | 5 | |
| DOI | https://doi.org/10.1051/bioconf/20201700201 | |
| Published online | 28 February 2020 | |
Information system for satellite monitoring of agricultural machinery using Wialon IPS communication protocol
Don State Technical University, Rostov-on-Don 344000, Russia
* Corresponding author: galushkavv@yandex.ru
The article is devoted to the urgent problem of developing an information system for monitoring the location and condition of agricultural machinery as part of the introduction of precision agriculture technologies in the activities of agricultural companies. It discusses the general principles of organizing the interaction of system components, such as GPS trackers, a web server and a client computer, defines the main stages of interaction and describes the communication protocols used at each stage. Special attention is paid to the consideration of the packet structure of the Wialon IPS protocol, which is used to transmit data on coordinates and other technical parameters. For this protocol, several methods have been proposed for parsing the contents of packets to extract useful information from them, both using standard functions of programming languages and using regular expressions. To protect the transmitted data, a two-way authorization algorithm is developed, its scheme is given and the main stages are described. The article also presents the approaches to the implementation of parallel processing of connections from a large number of GPS trackers to increase the overall efficiency of the system.
© The Authors, published by EDP Sciences, 2020
 This is an Open Access article distributed under the terms of the Creative Commons Attribution License 4.0, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
This is an Open Access article distributed under the terms of the Creative Commons Attribution License 4.0, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
1 Introduction
The agro-industrial complex, like any other complex multi-level system, requires effective management, which today is impossible without the use of information systems and technologies. Among the modern tools to improve the efficiency of agricultural production, precision agriculture [1, 2] occupies an important place. It is an integrated high-tech system of agricultural management, including global positioning system (GPS), geographic information systems [3], yield monitoring technologies, variable rate technology, remote sensing technology and the technology of the internet of things (IoT) [4, 5].
Global positioning technologies [6, 7] are used both at the initial stage of the implementation of precision agriculture system, which consists in the coordinate binding of fields to electronic maps, and at some later stages: the organization of parallel driving, control and accounting of fuel consumption, monitoring the state of agricultural machinery, etc. To implement these features, it is necessary to organize the joint work of at least two devices: a GPS-tracker and a centralized server that collects and processes information from trackers.
Existing large integrated information management system of agricultural production, such as cropio.com, agro-gps.ru or geomir.ru have ample opportunity for interaction with various models of GPS-trackers, but they provide the functionality may be overkill for small and medium enterprises. Other factors limiting the scope of these systems are the additional complexity of use for untrained users and the high cost. In this regard, for many agricultural enterprises, the task of creating their own system rises that implements the necessary set of these functions, based on the use of information technology becomes urgent.
2 General scheme of the organization of interaction of system components
The basis of this system is an application that performs the previously described functions of the server, but its operation is impossible without additional modules responsible for long-term storage and efficient processing of large amounts of data, as well as highly specialized modules designed to communicate with GPS-trackers. The general scheme of organization of interaction between the components of the system is shown in figure 1.
On this scheme it is possible to allocate 3 parts on each of which different technologies and protocols of communication are applied:
Between the satellite of the global navigation system and the tracker installed in the equipment, the standard GPS Protocol – NMEA 0183 is used.
Between the tracker and the server on the Internet. At this part, the coordinates of the equipment are transmitted, as well as the required parameters of its operation, such as the time since the start of the movement, the reliability coefficient of satellite data (HDOP), the values of acceleration sensors, temperature and voltage of the onboard network and others, depending on the specific model of the tracker. The Protocol by which this data will be transmitted to the server also depends on it. In this paper, we will consider a system for monitoring equipment based on Mielta GPS-trackers (models M1, M3 and M7), working on the Protocol Wialon IPS 1.1, taking into account the peculiarities of its implementation and additional commands available in these devices (mielta.ru).
The area between the server and the user – is a standard connection to the web-server via HTTP or HTTPS.
These protocols apply only to the upper level of the OSI model, and it is assumed that the protocols corresponding to the type of physical connection, switching and addressing methods will be used at the lower levels.
Among the presented protocols, the most interesting is Wialon IPS, as it is not widespread, unlike, for example, HTTP, and does not have ready-made programs for data exchange using IT.
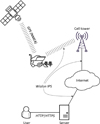 |
Fig. 1. System components interaction diagram |
3 Wialon IPS protocol
The Wialon IPS communication Protocol is designed for use in personal and automotive GPS and GLONASS trackers and is freely distributed under the terms of the GNU FDL. At the transport layer, Wialon IPS uses the TCP Protocol and any available port, both on the transmitting device and on the server. It supports data transfer in both directions. As a rule, from the tracker to the server the coordinates of the equipment and other parameters described earlier are transmitted, and from the server to the tracker – control commands. All data is transmitted in ASCII text format.
According to official documentation (gurtam.com) Wialon IPS 1.1 Protocol packet has the following format:
-
#TP#msg\r\n, in which
-
# – start byte,
-
TP – packet type identifier,
-
# -separator,
-
msg – directly message,
-
\r\n – the batch terminator.
There are 9 types of packets in the Protocol, each with its own message format. For each type, there is also a response packet that confirms the successful receipt of the message. Response packets are generally in a simpler format.
The main task of the server software is to process incoming packets, namely:
parsing the packet to highlight parts of the message,
packet type definition,
parsing the message text string according to the packet type,
extraction of useful data (in particular coordinates) from messages and transfer them for further processing,
sending confirmation of receipt.
4 Parsing messages
It is possible to notice that Wialon IPS packets have a relatively simple structure, and that the beginning, end, and boundaries between parts of the packet are clearly marked and indicated by control characters. On the other hand, the format of messages (the part previously designated as msg) transmitted within a packet is quite complex and varied, as it differs for different types of packets. These reasons lead to the need to use different parsing methods [8] at different stages of packet processing.
The selection of the packet type at the first stage is advisable to carry out using static analysis performed by standard string processing functions available in any programming language. This function using pseudocode can be written as follows:
type = substring(packet, 1, index_of(packet, “#”, 1)).
In the given command “substring” is a function of substring selection in a string. Its first parameter “packet” is the source data for substring selection. The second parameter of this function-the initial position, is taken to be 1, since the 0 position, according to the Protocol, is always a control character that is not used for the transmission of payload. The third parameter is the end position. To determine it, the “index of” function is used to find the position of the symbol specified as its second parameter. The source data for this function is also specified by the first parameter. The third parameter in this case is the position number from which the search begins. It must also be set to 1, because the delimiter character you are looking for is the same as the packet start character at position 0.
Unlike packet analysis, the task of parsing the messages contained in them is more complex because of the variable length of the messages, as well as their more complex internal structure. Consider the example of a reduced data packet that has the following structure:
#SD#date;time;lat1;lat2;lon1;lon2;speed;course;height;sats\r\n, in which
date, time – date and time when the packet was formed by the tracker,
lat1, lat2 – latitude (1st part contains coordinates, 2nd part indicates North or South latitude),
lon1, lon2 – longitude (1st part contains coordinates, 2nd part indicates West or East longitude),
course – deviation in degrees from the direction to the server,
sats – number of satellites, on the basis of information from which all other values are calculated.
Using the substring allocation function described above for this message format will require writing a large amount of poorly readable code, in which each line will be responsible for finding the desired fragment in the original message. More effective from the point of view of software implementation is the use of the function of splitting a string into an array of substrings:
M = split (message, “;”).
The second parameter of this function is the character used to separate the string. The Mi values from the resulting array can then be placed in the appropriate variables and used in data processing algorithms.
Parsing the example string, as well as fairly complex messages of other types of Wialon IPS Protocol, can be performed using regular expressions. Their advantage is flexibility and versatility, as well as a standard (PERL-like) syntax that is the same in different programming languages. Regular expressions are based on the use of wildcard characters, which form a pattern, which is used to find, replace or otherwise manipulate the substrings corresponding to it.
A regular expression to parse a reduced data packet will look like this:![$$ {{}^{\wedge}}\# \left[ {{\text{A}} - {\text{Z}}} \right]\left\{ {{{1}},{{2}}} \right\}\# \left( {\backslash {\text{d}}\{ {{4}}\} } \right);\left( {\backslash {\text{d}}\{ {{4}}\} } \right);\left( {\backslash {\text{d}} + \backslash .\backslash {\text{d}} + } \right);\left( {\left[ {{\text{N}},{\text{S}}} \right]} \right);\left( {\backslash {\text{d}} + \backslash .\backslash {\text{d}} + } \right);\left( {\left[ {{\text{W}},{\text{E}}} \right]} \right);\left( {\backslash {\text{d}} + } \right);\left( {\backslash {\text{d}} + } \right);\left( {\backslash {\text{d}} + } \right);\left( {\backslash {\text{d}} + } \right)\backslash /{\text{r}}\backslash /{\text{n}}\$ $$](/articles/bioconf/full_html/2020/01/bioconf_fies2020_00201/bioconf_fies2020_00201-eq1.gif)
Using this regular expression will also break the string into separate parts, however, unlike the previous method, it has several advantages. One of them is the automatic control of data types by specifying a character class \d, denoting only digits, or enumeration [N, S] admitting in this position only one of the two specified letters. It should also be noted that if you change the message format in the Protocol, it will be sufficient to rewrite the string with the regular expression instead of changing the program code used in the previous methods and recompiling the application.
Among the all types of packets, it is worth considering authorization packets and the associated authentication procedures of data exchange participants. In this case, it is necessary to take into account the peculiarities of the implementation of the Protocol Wialon IPS, available in a particular model of GPS-tracker, many of which can provide services in the server mode and also require authorization before accepting any messages, in particular control commands. This procedure is called bilateral authorization.
5 Two-way authorization
The procedure of data exchange between the GPS-tracker and the server, according to the classical model of client-server interaction, is always initiated by the client, that is, in this case, the tracker. In accordance with the Wialon IPS Protocol, when establishing a connection, the tracker first sends a login packet that contains a unique identifier of the tracker, which is usually the IMEI (International Mobile Equipment Identity) of the communication module installed in it, and a password. The password must be set by the administrator during the initial configuration of the tracker. The IMEI and password are credentials that must be stored in the server database and used to provide access to the server. In this case, the use of authorization allows avoiding getting to the server fake data that can be sent by an attacker in order to form false routes of movement of equipment, or simply load the server with a constant meaningless processing of packets containing random data, thereby significantly reducing its useful performance.
The next step in establishing a connection is authorization on the tracker side. The Wialon IPS Protocol does not provide for this special packet, as it is designed primarily for one-way data transfer to the server, but the considered models of mielta trackers have their own command for authorization:
pwd 12345, in which
12345-a password that must be replaced with a real value that meets the security policies of the organization, in particular regarding the length and complexity of the password.
All commands that are not included in the Wialon IPS Protocol, including the one considered and must be transmitted to the tracker inside TCP packets in plain text. In case of successful authorization the message “Welcome! User logged in”, for processing which there is no need to create a special algorithm, it is enough to use the standard for a particular programming language method of comparing strings.
The enlarged scheme of the two-way authorization algorithm is shown in Figure 2. In addition to the already described stages, it also contains blocks that indicate the time-out of the process of waiting for connections and waiting the server to receive a response packet from the tracker, the use of which is advisable in connection with possible communication interruptions and will allow the program not being in a state of endless waiting.
The algorithm can end with one of 3 results:
Unsuccessful authorization of the tracker on the server. With this result, further data transfer is not possible.
Successful authorization of the tracker on the server, unsuccessful authorization of the server on the tracker. This result will allow receiving data, including coordinates, but will not allow sending control commands to the tracker.
Full two-way authorization that allows data being exchanged in both directions.
From the above descriptions, it follows that in the future process of the program may require simultaneous execution of two actions: receiving incoming packets with data and sending outgoing packets with commands. Moreover, it should be borne in mind that at any given time a large number of trackers will be connected to the server, for each of which you will need to perform the listed actions, which leads to the need to implement parallel processing of connections.
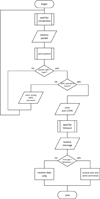 |
Fig. 2. Bilateral authorization algorithm diagram |
6 Parallel processing of connections
Modern operating systems and programming languages provide ample opportunities to create programs in which several actions [9] will be performed simultaneously. For this purpose, multithreading technologies [10, 11] are used, which technically consist in the fact that the computational process generated in the operating system can consist of several threads running in parallel, that is, without a prescribed order in time.
At the start of the program, at least one main thread is always created, all the others, if any, are considered child threads. Each new thread can also create its own child threads. Figure 3 shows a diagram of creating threads while the program is running. As you can see, all child threads can be divided into 2 types: data receiving stream and command sending stream. Their creation occurs as a result of the authorization algorithm described above.
The diagram also indicates the events that result in the generation of a new stream. For the data receiving flow, this event is the arrival of an authorization packet from the server, and for the command sending flow, it is the successful authorization of the tracker on the server. In this way, in case of failure authorization occurs premature interruption of the flow, and if successful, it enters an infinite loop waiting for data reception, which can be completed only at the command of the user.
Processing each connection in a separate thread will allow creating only 2 functions in the program: one for receiving data, and the second for transmitting, and run their copies as many times as connections from trackers will be initiated.
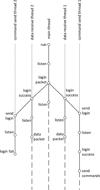 |
Fig. 3. Diagram of parallel processing of connections |
7 Conclusion
The described approach to the software implementation of the interaction between GPS-trackers and the Internet server using the Wialon IPS Protocol allows the effective collection of data on the coordinates of equipment and other parameters. On the basis of the data obtained, it is possible to monitor its movements in real time, as well as to maintain statistics for past periods to improve the quality of forecasts and management decisions. The development and implementation of the monitoring system of agricultural machinery using the proposed methods and algorithms provides agro-industrial enterprises with the opportunity to introduce modern means of informatisation, while it does not have significant economic costs and technical difficulties.
References
- L.P. Shatalina, AIC in Russia, 24(4), 949–953 (2017) [Google Scholar]
- A. Ju. Tjumakov, U.M. Sabo, A.I. Belenkov, Agrochemical bulletin, 4, 2–8 (2014) [Google Scholar]
- M.R. Yousefi, A.M. Razdari, Int. J. of Advanc. Biolog. and Biomed. Res., 2(4), 473–476 (2014) [Google Scholar]
- M. Dholu, K.A. Ghodinde, Int. Conf. on Trends in Electr. and Inform. (ICOEI), 339–342 (2018) [Google Scholar]
- A. Khattab, A. Abdelgawad, K. Yelmarthi, Int. Conf. on Microelectr. (ICM), 201–204 (2016) [Google Scholar]
- V.V. Borodychev, E.Je. Golovinov, M.N. Lytov, Ways to improve the efficiency of irrigated agriculture, 2, 48–52 (2016) [Google Scholar]
- N.S. Naik, V.V. Shete, S.R. Danve, Invent. Comput. Technolog. (ICICT), 2, 97–99 (2016) [Google Scholar]
- V.V. Galushka, D.V. Marshakov, V.A. Fathi, MATEC Web of Conf., 132, 05001 (2017) [CrossRef] [Google Scholar]
- E.I. Gladyshev, A.V. Murygin, Topical issues of aviation and astronautics, 1(8), 351–352 (2012) [Google Scholar]
- A.E. Azarov, V.A. Glagolev, Transactions of Institute of social and humanitarian knowledge, 15(2), 21–25 (2017) [Google Scholar]
- R. Ingles, P. Perek, M. Orlikowski, A. Napieralski, Mixed Design of Integrated Circuits & Systems (MIXDES), 153–157 (2015) [Google Scholar]
All Figures
 |
Fig. 1. System components interaction diagram |
| In the text | |
 |
Fig. 2. Bilateral authorization algorithm diagram |
| In the text | |
 |
Fig. 3. Diagram of parallel processing of connections |
| In the text | |
Current usage metrics show cumulative count of Article Views (full-text article views including HTML views, PDF and ePub downloads, according to the available data) and Abstracts Views on Vision4Press platform.
Data correspond to usage on the plateform after 2015. The current usage metrics is available 48-96 hours after online publication and is updated daily on week days.
Initial download of the metrics may take a while.



